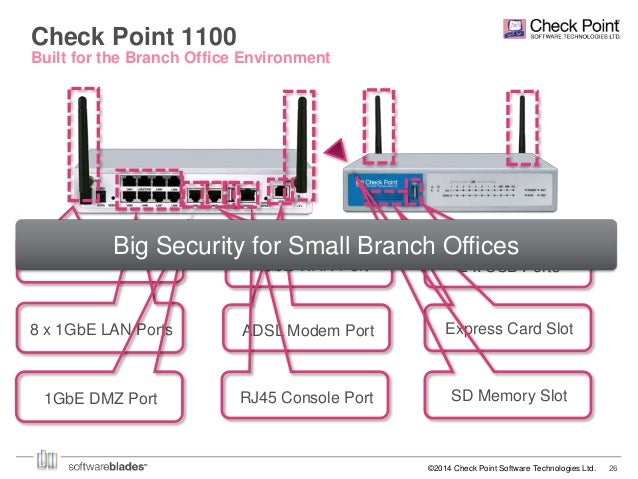
Checkpoint Security Conversion Tool
A GARTNER LEADER FOR THE SIXTH CONSECUTIVE TIME Next-generation firewalls are far superior to – and more secure than – traditional firewalls. Having moved beyond port and protocol filtering, today’s NGFWs boast safe enablement of applications, classification of traffic, ease of management, fewer rules, lower TCO and, of course, better security. No longer an optional part of security infrastructure, next-generation firewalls are a must-have for today’s organizations.
Gartner just released its 2017 Magic Quadrant report for Enterprise Network Firewalls and named Palo Alto Networks® a Leader for Enterprise Network Firewalls for the sixth time. Read this year’s report to: • Get a wide-angle view of the relative positions of the market’s competitors.
• Ascertain how well vendors are executing their stated visions and performing against Gartner’s market view. • Learn what to consider when making purchasing decisions. Lsi Megaraid Storage Manager Windows 7.
Gartner, Inc., a leading global research and advisory company, provides IT leaders with the objective insights they need to make informed business and purchasing decisions. The Gartner Magic Quadrant for Enterprise Network Firewalls report provides a comprehensive overview of the market, including research and key players. Based on a uniform set of evaluation criteria, the graphical grid format provides an understanding of how established vendors are executing against their own stated visions as well as a visual representation of Gartner’s market view. The quadrant encompasses Leaders, Visionaries, Niche Players and Challengers. Palo Alto Networks ® has been firmly positioned in the top-right quadrant as a Leader for six years in a row. We believe Palo Alto Networks Next-Generation Firewall is the foundational component of the company’s natively integrated Next-Generation Security Platform. Rooted in prevention, the platform combines network, cloud and endpoint security capabilities to safely enable applications and prevent successful cyber breaches wherever your organization’s data resides.
Cisco Security Conversion Tool (sct.exe). Cisco Security Conversion Tool (SCT) is a software program to assist in converting a Check Point Firewall configuration into.
Gartner Magic Quadrant for Enterprise Network Firewalls, Adam Hils, Jeremy D’Hoinne, 10 July 2017. Gartner does not endorse any vendor, product or service depicted in its research publications, and does not advise technology users to select only those vendors with the highest ratings or other designation. Gartner research publications consist of the opinions of Gartner's research organization and should not be construed as statements of fact.
Gartner disclaims all warranties, expressed or implied, with respect to this research, including any warranties of merchantability or fitness for a particular purpose.
Git clone -- recursive https: //github.com/GoSecure/Cisco2Checkpoint c2c Instructions can be found on the. How does it work? The tool imports a Cisco ASA or IOS running-config file and converts it to a file that can be parsed by, a tool provided by Checkpoint to automate tasks. The converter supports objects including: Checkpoint objects Cisco syntax hosts/networks/ranges « object network » services « object service » hosts/networks/ranges groups « object-group network » service groups « object-group service » firewall rules « ip access-list », « access-list » For instance, be the host definition below from an ASA config file. # Number of hosts (imported from cisco file): 149 # Number of hosts (imported from checkpoint xml): 0 # Number of hosts (dynamically created): 168 # Number of hosts (after merge/cleanup): 0 # Number of subnet (imported from cisco file): 63 # Number of subnet (imported from checkpoint xml): 0 # Number of subnet (dynamically created): 36 # Number of subnet (after merge/cleanup): 0.